Command and control operations for commanders in the realm of Intel Analysis/Command and Command missions are undergoing a substantial transformation, marked by heightened demands driven by several key factors. The proliferation of information and sensor sources, an expanding array of stakeholders, and intricate workflows have necessitated a paradigm shift towards advanced technology platforms to facilitate efficient information distribution.
The Status Quo: Current Issues
- Isolated Feeds: One of the prominent challenges lies in the utilization of existing systems that rely on air-gapped, stove-piped network feeds. This approach, while once deemed secure, now presents formidable challenges for operators. The isolation impedes the seamless flow of information, leading to delays, inefficiencies, and a fragmented operational landscape.
- Cluttered Operator Spaces: The physical separation of classifications within operator spaces emerges as a complex issue. The traditional approach to categorizing and segregating information creates an environment where operators grapple with the difficulty of managing and accessing data across different security classifications. This physical clutter hampers the agility required for swift decision-making in dynamic mission scenarios.
- Limited Scalability: The current systems face a critical hurdle in terms of scalability and adaptability. As mission requirements evolve, the existing infrastructure struggles to scale or reconfigure easily. The key factors hindering scalability include hardware limitations, complex integration processes, software incompatibility, budgetary constraints, legacy system dependencies, training requirements, regulatory compliance and security concerns,
- Insider Threats: The escalating risk of insider threats, particularly with the accessibility provided by USB 2.0, adds a layer of vulnerability to command and control operations. The potential for unauthorized access or data breaches through this channel poses a significant concern, requiring a proactive approach to mitigate the insider threat landscape.
In essence, the challenges encompass not only the sheer volume and complexity of information but also the structural and technological constraints inherent in the current command and control landscape. Addressing these issues is imperative for commanders to navigate the evolving nature of their missions effectively and ensure a streamlined and secure operational environment.
Revolutionizing Command and Control: Thinklogical‘s Solutions for Scalability, Security, and Seamless Collaboration
Commanders can effectively address the challenges posed in command and control operations by leveraging next-generation AV infrastructures, These infrastructures feature scalable fiber optic KVM and VDS C2 systems, allowing operators to control multiple computers and collaborate efficiently in multi-level security environments what are the benefits to this solution?
- Unified Connectivity with Multi-Domain VDS: This eliminates the barriers imposed by isolated feeds, enabling seamless sharing and distribution of information across different security levels, ensuring commanders have a consolidated and coherent view of data, breaking down the silos that typically hinder efficient decision-making.
- Efficient Collaboration: The need for operators and analysts to collaborate with others, and the obstacles associated with the limitations of legacy C2 systems, have motivated the implementation of next-generation AV infrastructures that enable flexible and universal operator control and collaboration in multi-level security environments.
- Scalability and Flexibility: Thinklogical’s solutions provide a comprehensive and adaptable approach to addressing the factors hindering scalability in command and control systems. By offering modular architectures, compatibility, security assurances, and cost-effective scalability, Thinklogical empowers commanders to overcome the challenges associated with adapting to evolving mission requirements in a dynamic operational landscape.
- Enhanced Security Measures: The accredited multi-level security use of the Thinklogical solution ensures that data remains protected. At the heart of the system is a matrix switch accredited for use in multi-level security environments. In this model, most, if not all, computer and AV resources can be housed in a secure IT rack room and are extended to the users using IA-accredited KVM hardware. With this capability, these resources may be pooled, shared, and accessed as needed by operators with permission to do so.
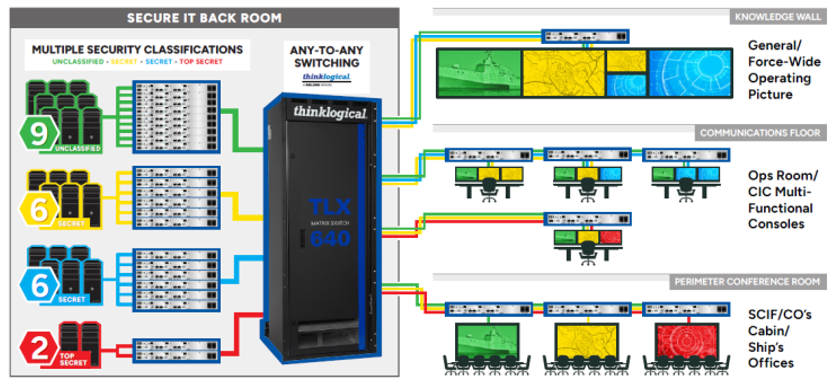
Thinklogical’s innovative multi-domain, multi-classification VDS and KVM technology presents a transformative solution to the challenges faced by commanders in the modern landscape of Intel Analysis/Command and Command missions. By addressing issues such as isolated network feeds, cluttered operator spaces, limited scalability, and insider threats, Thinklogical empowers commanders with a comprehensive and streamlined approach to command and control operations.
Thinklogical’s commitment to security, scalability, and flexibility positions commanders to navigate the complexities of modern warfare with confidence, ultimately leading to more effective and well-informed mission outcomes.

