By Nicholas Scheurkogel
This powerful statement is often repeated across the defence industry, and within the Department of National Defence (DND) and Canadian Armed Forces (CAF); so often over the past few years that many have come to believe that it is true. Why would it not be true? Computer hackers and foreign states can manipulate vulnerabilities in the programming of platforms to exploit ships, aircraft, armoured vehicles and body cameras on soldiers. Through cyber, it is possible to disable whole fleets of ships, force all drones to fall from the sky, and to manipulate the supply chain of key weapons platforms so that the mission fails just at the right time! What an adversary can do with their advanced cyber capabilities is endless and limited only their imagination.
… Or is it?
Is cyber the most significant threat? Is what adversaries can do with cyber endless and limited only by their imagination? Can an advanced adversary use cyber attacks to affect systems at the time and place of their choosing? There are a number of misconceptions that are commonly found in cyber-related discussions concerning the battlefield that are the basis for how cyber threats are mischaracterized. This mischaracterization often leads to the development of conceptual frameworks and outcomes that adversely impact the interests of the DND/CAF and the Defence Contactor Industry. Examples include the incorrect application of security controls for Information Technology (IT), the disruption of major projects, a reduction in operating capability, and an overall increase in the complexity of engineering efforts. These outcomes are caused by confusion between what is possible and what is likely, the application of corporate IT standards into the military environment, a false correlation between the value of the asset and the volume of required security measures, and finally, underestimating the scope, scale, and speed of possible cyber targets on the battlefield.
The question that will be explored in this article is simple: How do we approach framing and understanding the cyber threat with respect to engineering weapon systems and information-driven combat systems? As hinted above, the solution is not to be fearful of the unknown or to apply frameworks that do not represent the reality of how offensive and defensive cyber operations work. The proposed approach is to understand – and consider – key factors that will define the capabilities, intents, and opportunities available to any attacker.
Key Factors
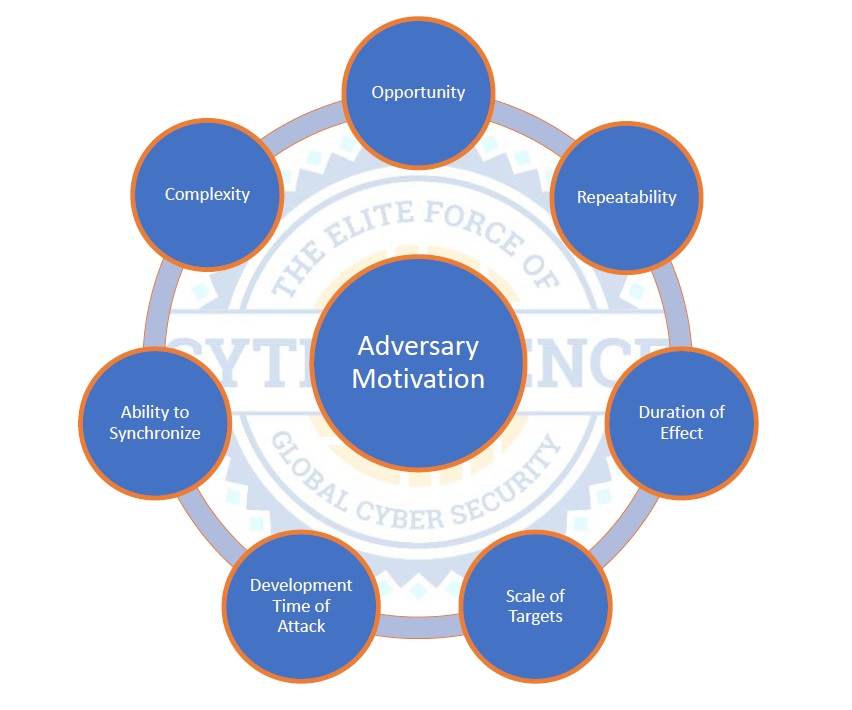
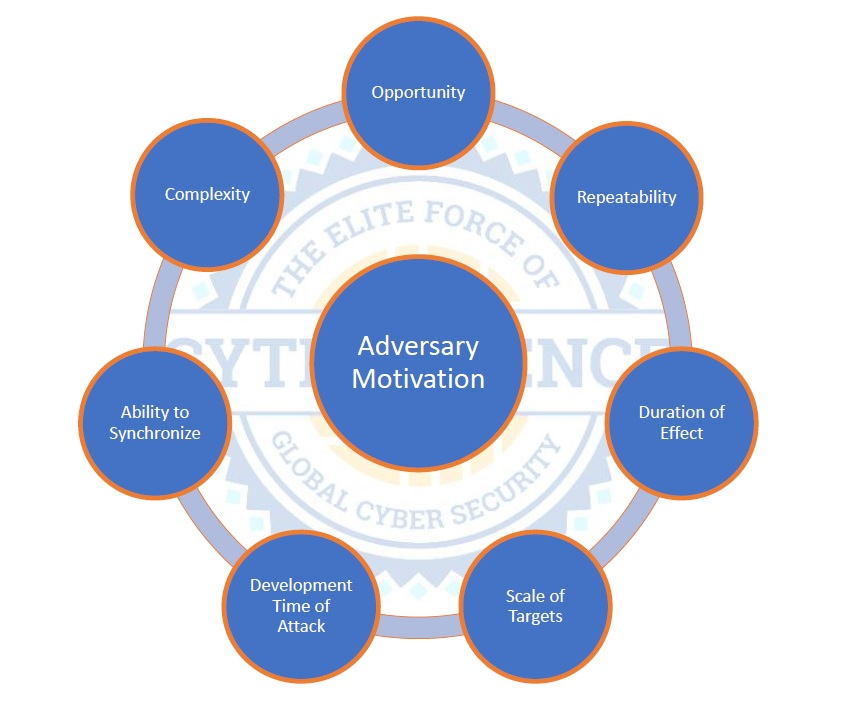
The classical view of threat is a combination of adversary intent, capability, and likelihood. This overall model is completely valid within the cyber environment as people and human motivations are always involved. Actions take planning, resources, and time that no adversary can afford to waste. Therefore, when determining the threat to a specific system, the methodological approach must consider those factors that realistically influence the adversary’s ability or motivation to attempt some type of cyber attack, which is centered squarely on the basic concept of return on investment (ROI). Is the investment worth the outcome? In order to answer this question, Cytelligence has developed advanced threat models based on the following factors that are used to project realistic and usable threat intelligence for weapons platforms and deployed operations. These assessments can be used to inform security, investments, and operational decisions for systems that are under development and in operations.
Opportunity: In order to attack a given system, an adversary must have an opportunity that allows him or her to identify a target, understand the target, weaponeer the most feasible form attack, and execute the attack in some useful fashion. Having a weaponeered attack without the ability to deploy it is useless. Consideration: Non-technical safeguards or operational choices can have a significant effect on the level of effort required by an adversary to create opportunities. Increasing effort reduces adversary ROI.
Complexity: Weapons systems are often highly complex machines. This complexity becomes an increased cost and level of effort for potential attackers. Although it is true that complex system can also, consequently, have more of an attack surface, leveraging that attack surface in a useful and predictable way requires the attacker to invest in overcoming a large percentage of that complexity. Consideration: Complexity directly relates to all other factors. Complex actions are often less repeatable, require more development time, are harder to synchronize and can vary on how long they may be effective.
Repeatability: Cyber attacks that can be repeated are significantly more useful than those that can only be executed a single time. Technically, it may be possible to repeat an attack, although practically, a military entity that suffers a cyber attack is very likely to take immediate action to prevent that attack from achieving success in the future. Once defences are in place against a given attack, there are potentially large components of the development effort that will not be reusable. Consideration: The degree of perceived repeatability will directly influence an adversary’s willingness to invest in developing and executing a cyber attack. There is little ROI if an attack takes many years to develop and can only be used once.
Duration of Effect and Defender
Recoverability: The likely duration of any effect caused by a cyber attack is central to adversary ROI calculation. Everyday, the world sees thousands of denial-of-service attacks, yet only a few are significant enough to be mentioned in the media. Most of these events are insignificant because they are only active for very short periods of time. Effects that can be maintained indefinitely are rare within the cyber environment. Similarly, if a defender can recover from the effect quickly, the value of executing the attack is greatly reduced. Consideration: Making design choices that reduce an attacker’s ability to sustain an effect over time reduces their ROI and therefore the threat to that system.
Ability to Synchronize Effects: The ability to synchronize effects is the most significant planning consideration for an adversary. It is rare that a random effect is useful. Without the ability to synchronize an effect and therefore leverage the effect efficiently, ROI is greatly reduced, often in favour of other tools that produce near term and consistent results. Consideration: When looking at potential cyber threats, the examination of non-cyber means of effecting the same outcome is critical. In many cases, guaranteed kinetic kills are more effective to synchronize than some forms of disabling cyber attacks.
Attack Development Time: There is a direct correlation between the speed at which an attack tool can be developed and the tactical utility of any adversary activity. Development time reduces operational flexibility by creating a delay between when an adversary wishes to cause an effect and when that effect can be realized. Consideration: Safeguards that force an adversary to continually invest in development efforts for an attack tool can greatly reduce adversary ROI.
Scale of Targets: Multi-national battlefields possess significant diversity and complexity in terms of deployed systems. The challenge that this presents an adversary is that they must choose where to allocate finite efforts. That choice must allow them to execute an effect that hits a useful target, for a useful duration, and at a definable time. This choice must have an acceptable degree of complexity and require an acceptable degree of access. There must also be opportunities. Consideration: Adversaries cannot target all systems all the time. Their choice will be dictated by their desired operational outcome and the factors listed above. Threat assessments must consider other systems that have a higher ROI for a given attacker.
The development of future capabilities for the CAF is an activity of tremendous national significance. Although cyber threats are real and can have an effect on capabilities in development and in operation, the key factors listed above must be understood if those threats are to be properly contextualized. Cyber threats on the battlefield will have similarities with what is commonly seen on the Internet but they are likely to manifest differently in conflict and therefore demand different solutions. Security decisions must be informed by contextually accurate threat assessment in order to avoid increasing costs, maximize operational freedom of action and enable capability delivery.
There are few organizations or resources who have the experience and capabilities to perform threat assessments for the defence environment. Traditional IT threat assessments don’t have the contextual knowledge and experience within the defence industry to build a strategy that yields meaningful results. Addressing the skill gap needs to be a focus for government, defence contractors, and industry.
Nicholas Scheurkogel is the Director of Cyber Intelligence at Cytelligence Inc. Prior to joining Cytelligence Nicholas led key cyber intelligence capabilities for the Department of National Defence (DND) including strategic cyber assessment, tactical support to cyber defence teams, and intelligence operations.